Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- Support
- :
- Support
- :
- Knowledge
- :
- Support Articles
- :
- Qlik Cloud: Information needed to troubleshoot SAM...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Qlik Cloud: Information needed to troubleshoot SAML authentication
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Qlik Cloud: Information needed to troubleshoot SAML authentication
Mar 29, 2024 12:51:05 AM
Mar 29, 2024 12:51:05 AM
Disclaimer: In Qlik Cloud, SAML is a supported authentication method that can be used. However the infrastructure to make SAML works will need to be set by the customer. Please be aware that Qlik Support can not help in the setting up of SAML/SSO or related issues. If the customer needs help to set up SAML from scratch, Qlik Consulting needs to be invoked. This is out of scope for Support.
Qlik Support will do a first assessment of SAML related support cases in order to understand if the issue is related to a possible defect in the implementation of SAML in Qlik Cloud or a wrong setup.
This article gathers information needed for Qlik Support to assess a SAML related support case.
Environments:
Considerations
The following need to be considered for the SAML implementation in Qlik Cloud:
- Encrypted SAML Assertions are not supported: please make sure that the SAML assertion is not encrypted (ADFS is one of the Identity Providers that have assertion encryption enabled by default). Regarding the signature, you can either sign the whole SAML response or just the SAML assertion.
- The ACS URL (also called "Reply URL" "Sign-on URL" based on the Identity Provider) should be set to https://<tenant_URL>/login/saml
- SAML Single logout (SLO) is not supported in Qlik Cloud. You will not be logged out of your Identity Provider automatically when logging out of Qlik Cloud.
Information needed
The following six pieces information are required when investigating a SAML-related issue:
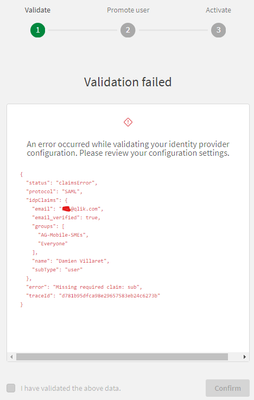
- A screenshot of the error encountered when trying to log in. Below is an example (Fig 1).
If a traceId number is provided in the error, please also provide the traceId in text format.
- The SAML Identity provider used (ADFS, Okta, Azure, Onelogin, etc.)
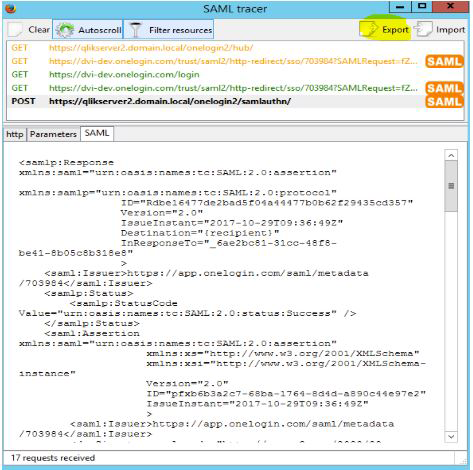
- Export of SAML trace logs
This can be collected using a browser extension such as SAML Tracer for Firefox or for Chrome on the client that is trying to log in using SAML. The below image highlights how/where to export SAML trace logs.
This is a very important piece of information, as without these logs it is not possible to tell what is happening when the user actually tries to authenticate! - Screenshots of how SAML has been set up in the Qlik Cloud console
- The SAML Identity provider metadata file