Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- Support
- :
- Support
- :
- Knowledge
- :
- Support Articles
- :
- How to configure Qlik Cloud with Okta
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
How to configure Qlik Cloud with Okta
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to configure Qlik Cloud with Okta
Nov 9, 2023 5:36:36 AM
Apr 19, 2022 10:57:35 AM
This guide provides the basic instructions on configuring Qlik Cloud with Okta as an identity provider.
This customization is provided as is. Qlik Support cannot provide continued support of the solution. For assistance, reach out to our Professional Services or engage in our active Integrations forum.
Configuring Okta
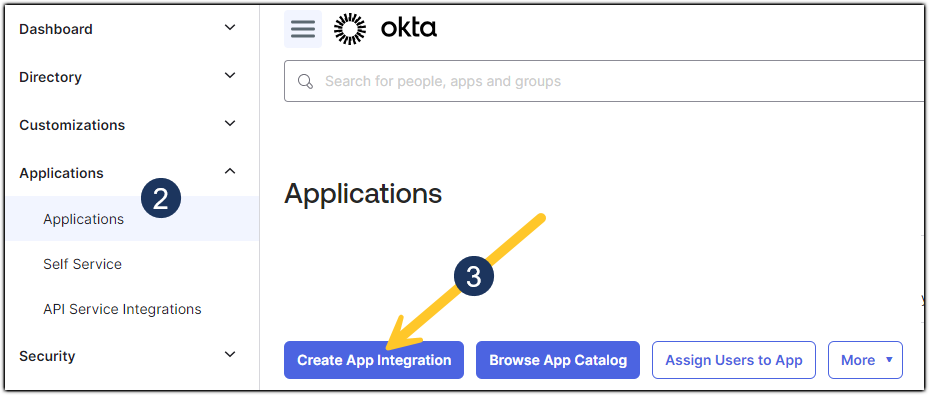
- Go to your Okta Admin Console
- Navigate to Applications
- Click Create App Integration
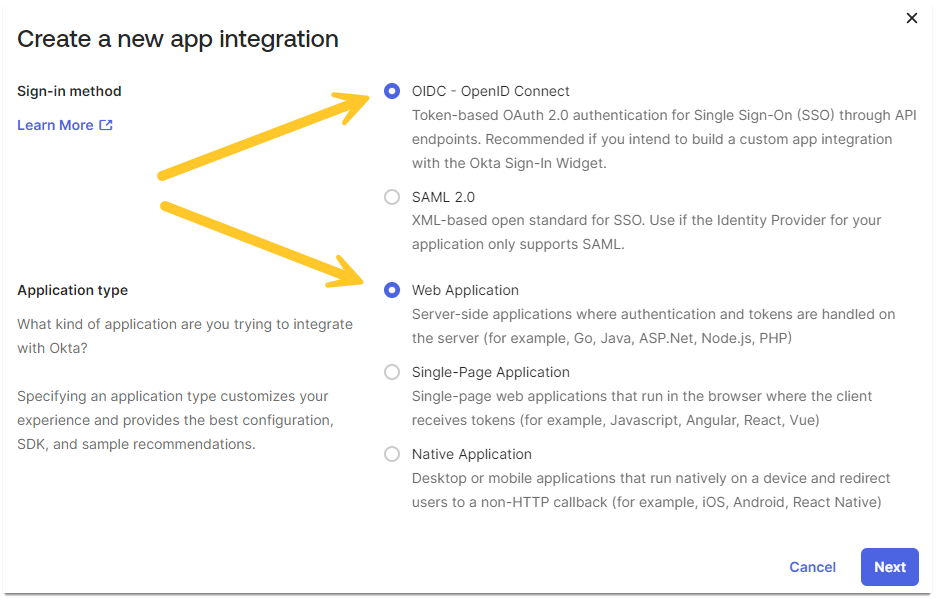
- Choose OIDC - OpenID Connect and Web Application, then click Next
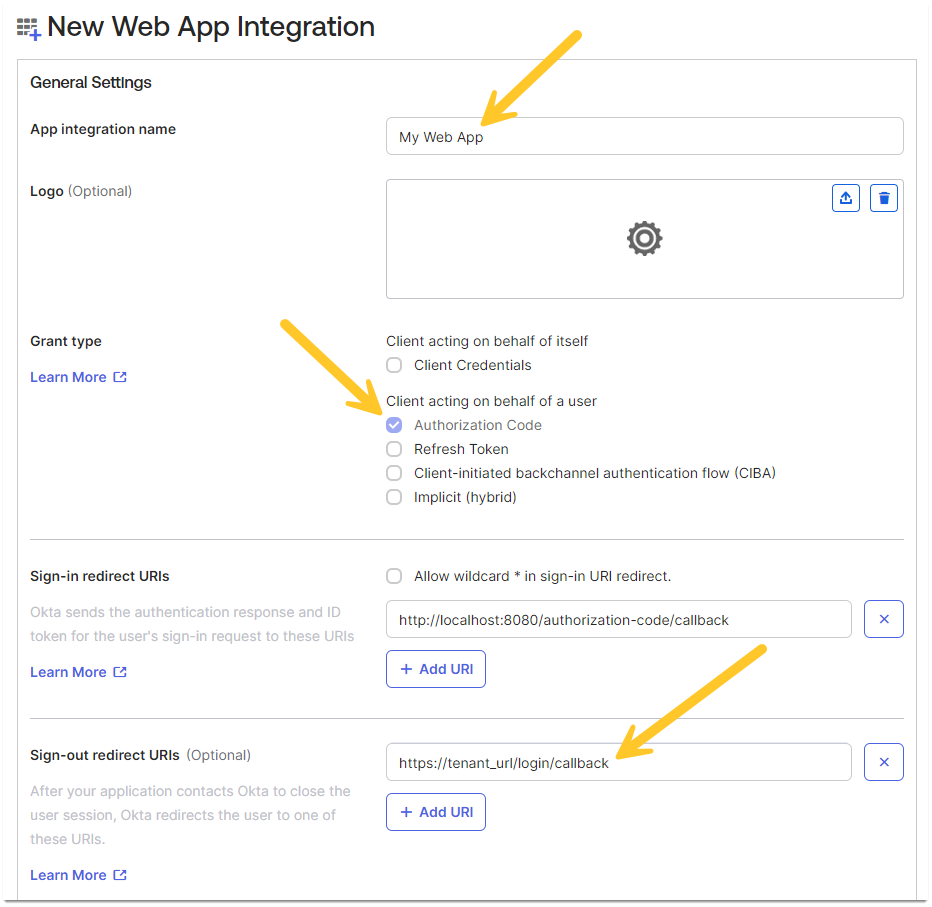
- Fill in the App Integration Name (this name identifies the application)
- Set Grant type to Authorization Code
- Enter your tenant URL in Sign-out redirect URIs, adding /login/callback
Example: https://tenant_url/login/callback
This must be the actual tenant name, not the alias.
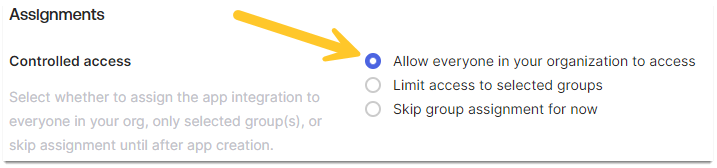
- Scroll down to the Assignments section. Set Allow everyone in your organization to access
- Click Save
- Copy the Client ID and Client Secret. Both are needed when configuring the IdP on the tenant.
- Switch to the Sign On tab
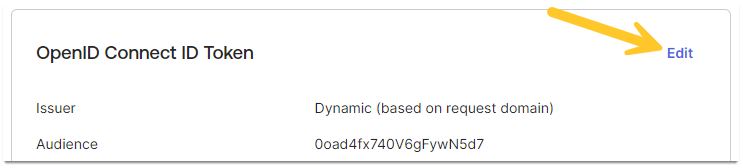
- Click Edit on the OpenID Connect ID Token
- Set Issuer to the Okta URL
- Set Group claim type to Filter
- Set Group claim filter to groups, followed by Matches regex and .*
- Click Save
- The next step is to add an Authorization Server
If you do not have access to Okta's API Access Management, see Using a custom Authorization Server for Okta in Qlik Cloud.
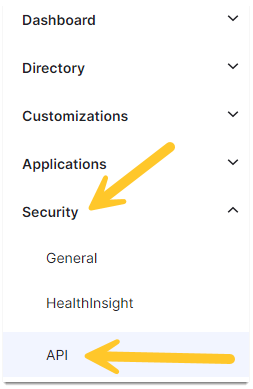
- Expand the Okta admin panel menu
- Expand Security and open API
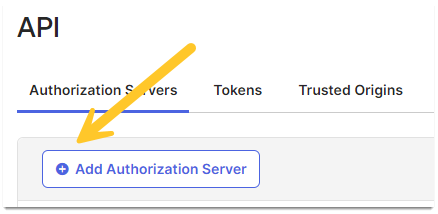
- Click Add Authorization Server.
- Set Name to QlikAPI (example)
- Set Audience to qlik.api
- Set Issuer to Okta URL
- Leave everything else default, then click Save
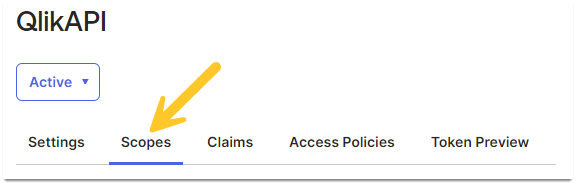
- Switch to the Scopes tab
- Click Add Scope
- Set the Name
- Set a Display phrase
- Set a Description
- Set User content to Implicit
- Mark Set as default scope
- Leave Include in public metadata unchecked
- Click Save
- Switch to Access Policies
- Click Add Policy
- Set a Name
- Set a Description
- Set Assign to to All clients
- Click Update Policy
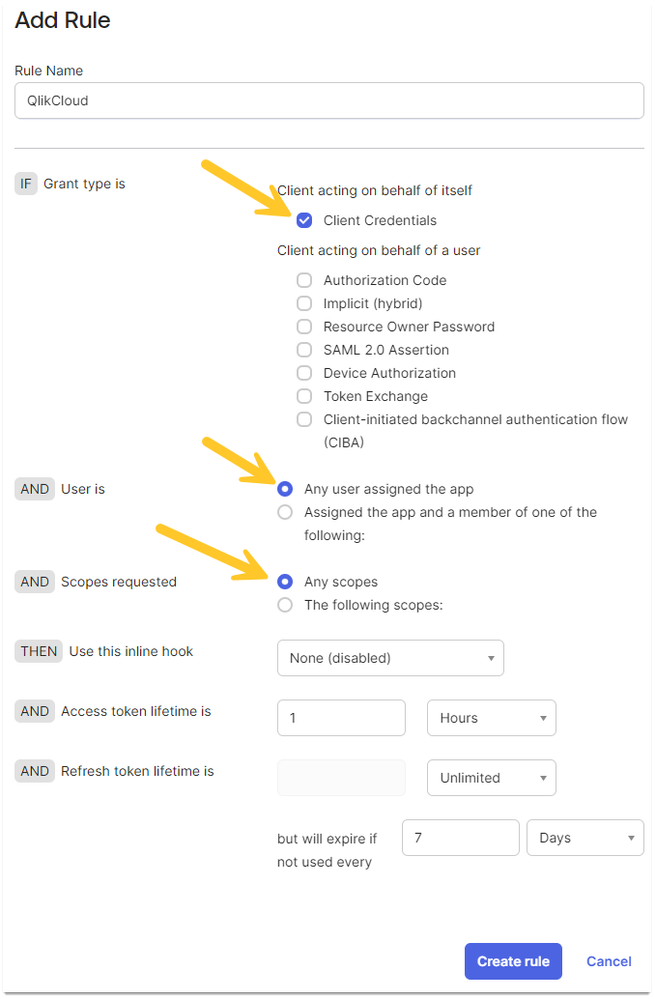
- Click Add rule
- Set a Rule Name
- Check Client Credentials
- Uncheck all items under Client acting on behalf of a user
- Check Any user assigned the app
- Check Any scopes
- Leave the remaining settings at default
- Click Create rule
- Check Clients Credentials, Any user assigned the app and Any scopes then click Update Rule
Configuring Qlik Cloud Tenant
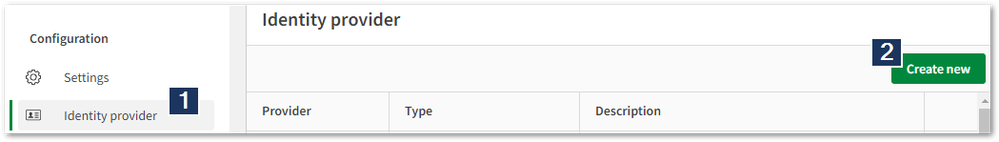
- Open the Qlik Cloud Management Console and browse to Identity Providers
- Click Create New
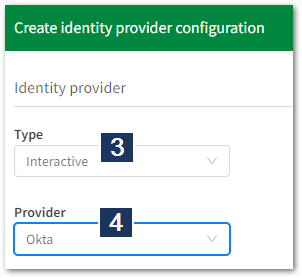
- Choose Interactive
- Choose Okta
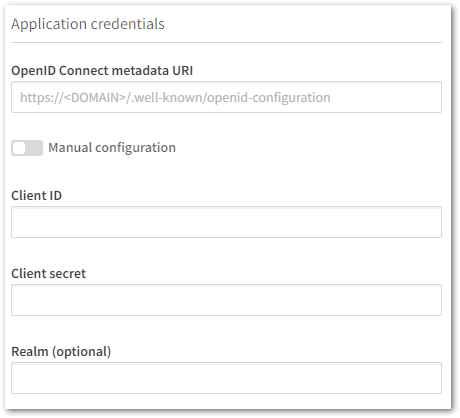
- Fill out the Application credentials as per the Okta Setup
- Provide your claims mapping as per your setup
- Click Create
For additional information on how to create new identity providers in Qlik Cloud, see Creating a new identity provider configuration.
Environment:
The information in this article is provided as-is and to be used at own discretion. Depending on tool(s) used, customization(s), and/or other factors ongoing support on the solution below may not be provided by Qlik Support.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Luis
Please give me a advice.
I followed the steps you provided and set it up.
However, there is no button of "Add Authorization Server" at regarding "12.Then click Add Authorization Server...".
So I have the follwing two questions.
1) Is the procedure different in the latest Okta version?
2) Please let us know the procedure to follow with the latest version.
Best regards.
Hideaki.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I have the same concern as Hkatsu. We have not purchased Okta's API Access Management so we do not have access to the Add Authorization Server option. Our other integrations are SAML so it has not been needed. It seems like there should be an alternate setup option that doesn't result in spending lots of extra money.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Catarina has put together a workaround for you and we've recently published and verified it. Here you go! Using a custom Authorization Server for Okta in Qlik Cloud
All the best,
Sonja
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Excellent @Sonja_Bauernfeind . Thanks for following up and I'm eager to test it out. I'll follow up after I get a chance to set it up.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Luis_Arocho-LLantin @Sonja_Bauernfeind can you make a small change in the document. Step 5 says you need to enter the tenant name:
Fill in the App Integration Name, chose Authorization Code and enter your tenant name adding at the end /login/callback
Might be good to mention that it's NOT the alias name. We struggled with setting it up and were getting the error the the RETURN_URI wasn't linked to a login page. This was just because were using the tenant alias hostname (companyname.eu.qlikcloud.com) instead of the tenant hostname (xy6shdh.eu.qlikcloud.com shown in the about screen)
Could be that this is clear for most of the qlik admins, but it took me few hours before finding the cause of it. Qlik Support wasn't even able to help me with this.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @obeyaztas
Thank you for closing the loop with us on this! I updated the article as you suggested (and am actively working on updating it in general).
All the best,
Sonja
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Sonja_Bauernfeind , we found another piece that may be missing. For us, we needed to expand the Advanced Options on the Qlik setup and add "groups" into the scope even though we mapped it correctly in the claims section. Without this we weren't pulling in any groups through Okta to our tenant.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thank you, @mshann01 I will review this during my article update.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi @Luis_Arocho-LLantin and @Sonja_Bauernfeind I tried the integration and got the error below.
Error: The 'redirect_uri' parameter must be a Login redirect URI in the client app settings: