Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- Support
- :
- Support
- :
- Knowledge
- :
- Member Articles
- :
- Manage GCP Group with Qlik Automation
- Edit Document
- Move Document
- Delete Document
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Manage GCP Group with Qlik Automation
- Move Document
- Delete Document and Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Manage GCP Group with Qlik Automation
Mar 23, 2023 6:56:03 AM
Mar 23, 2023 6:56:11 AM
Problem
By the time I’m writing this article Qlik Cloud Service does not support yet the GCP user group during the authentication phase. Thus allow GCP users to access Qlik Cloud, base on their groups is not (yet) an option.
This is expected to be a temporary situation and Qlik will deliver soon (or later) also this feature. Nevertheless timing is important and it may avoid the SaaS adoption for Qlik enthusiast with the hard constraint to relay on Google groups.
In the context above, in this article I'm going to propose an alternative way to achieve the same business scope granting users to spaces based on their membership groups. Therefore, acting on the Authorization instead, the Authentication. This solution is imperfect, widely improvable (anyone is welcome to contribute) and to some extent graceless, but it just works and sometime could make the difference between adopting Qlik SaaS or something else.
Environment
- Qlik Cloud Service
- Qlik Application Automation
- GCP Directory API
Resolution
Any authenticated user (through GCP or any other solution) will land on Qlik Cloud creating a new user for their first access. This solution is triggered on that specific event “User Creation”. Qlik Application Automation is triggered on the User creation event, and go through the following steps
- Invoke the Google Directory API and retrieve the list of authorized users.
- Check the new created user is among this list.
- If the user is authorized to access, then assign a license and grants for the authorized spaces.
- If the user is not authorized, then the automation disables it.
Google API Call
Here you can find the Google API documentation . The HTTP request retrieve a paginated list of users belonging to the same {groupKey}. This HTTP request needs an authentication method, for this you need to create a service account on the google platform.
- Follow the instruction here to get the user account, the private key and the private key id.
- Set the start Block as:
- Run Mode : Webhook
- Connector : Qlik Cloud Service
- Event : User Created
- From the Qlik Cloud Service Connector use the Get User Block to get the user details from the user just created
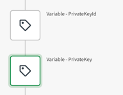
- Next step is getting the Bearer Token for the REST call. Use two variable blokes to store the Private Key and the Private Key Id.
Pay attention to paste the Private Key. It is made of 3 lines. The first line is the “BEGIN PRIVATE KEY” the second line is the key itself without any carriage return line feed, the third line is the “END PRIVATE KEY” line. You should end up with something like this:
-----BEGIN PRIVATE KEY-----
<Your private Key in one single line, remove all the CR+LF or /n>
-----END PRIVATE KEY-----
- Use a custom code block to get the Bearer token. You need to pass 3 inputs to the custom block
Private Key id from the variable
Private Key from the variable
Time as: {number: {date: 'now', 'U'}}
Select Python as language and paste these lines:
import jwt
iat = inputs['time']
exp = iat + 3600 * 1000
payload = {'iss': 'qlik-user-sync@qliksaasidp-377811.iam.gserviceaccount.com',
'sub': 'qlik-user-sync@qliksaasidp-377811.iam.gserviceaccount.com',
'aud': 'https://admin.googleapis.com/',
'iat': iat,
'exp': exp}
additional_headers = {'kid': inputs['Private Key Id'],"alg": "RS256","typ": "JWT"}
signed_jwt = jwt.encode(payload, inputs['Private Key'], headers=additional_headers,
algorithm='RS256')
print (signed_jwt)
For more details please check this page.
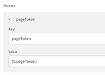
- Next steps need to manage the multipage. Use a new variable, call it pageToken and set as empty string.
- The following 3 steps get the number of users the query will retrieve and create an array with the number of pages to read.
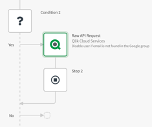
- Inside the Loop, as first step let’s call the Google Directory API. Use the Call URL Block. You can find the documentation on how to use it at this page.
Remember to use as parameter the pageToken
And in the header the authorization Bearer as follow:
- Next step is updating the nextPage Token for the next iteration:
- Loop over the list of members coming from the API Call.
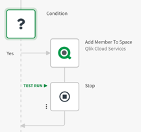
- Now, for each iteration we can finally check if the user just created is in the list with a simple condition Block. If it is in the list, we can assign a license and grant the user to one or more spaces. If it is not, just go for the next iteration.
- Once the iterations on the pages is over and the user was not found, we know he/she is not among the list of authorized users, thus we can get further action such as disable it.
Here attached to this article you can find the Automation. Remember to replace the placeholder in the Variable Private Key Id and Variable Private Key with your own keys as well as the group in the two call url blocks.
- Move Comment
- Delete Comment
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Vincenzo_Esposito thanks for creating this documentation. I had a question about its functionality. Is the idea that only 1 Google IDP group is queried? If I want to use Google's IDP groups to control who has access to which space (for example, a Sales group in Google will have access to a Sales space in Qlik, and then a Finance Google group will have access to the Finance space in Qlik), is that achievable with your workaround?